|
In Line with International Information Security Standards |
|
 |
|
Information Security Guidelines |
Information Security Responsible Unit |
Giant will strengthen information security management and establish the "Security Promotion Committee" starting in 2023, serving as the company's dedicated security advisory unit. This committee is responsible for planning and developing goals, strategies, and management procedures for information security, as well as promoting and overseeing the implementation of the overall security system. In terms of organizational structure, the President serves as the "Information Security Director" and convenes the committee, further assigning the "Information Security Officer" and members of the "Information Security Audit Team." The cybersecurity officer is responsible for organizing the "Information Security Execution Team" and the "Emergency Response Team" established as needed for tasks. These three groups each undertake different tasks, responsible for promoting and enforcing the cybersecurity system, conducting audits on its implementation, and promptly responding to and tracking it in case of cybersecurity incidents.
|
Information Security Risk Management |
To effectively manage the risks associated with Giant's Information Security Management System (ISMS), the company established the "Risk Assessment and Management Procedure.
 |
|
 |
|
 |
|
 |
|
 |
|
|
Information Security Education and Training |
Planned by the "Information Security Execution Team." Both internal and external personnel are required to participate in relevant training based on their job responsibilities.To enhance all employees' awareness and ability to protect themselves in information security, we conduct regular information security training every year to ensure that every colleague has the basic ability to identify and prevent information security risks.
The training content covered basic concepts of information security, trends in security threats, incident response methods, and daily guidelines for secure information practices. Through this, employees’ vigilance and response capabilities in the face of potential information security risks are enhanced, and the correctness and safety of operating information equipment in the workplace are strengthened.In addition to regular training, the company has also established an Information Education and Training Statistics Table as the basis for tracking course participation and training outcomes and incorporated it into the Information Security Management System. To grasp external information security threats in real time, the company conducts daily monitoring of vulnerability alerts from the National Institute of Cyber Security (NIST) and notifications from the Taiwan Computer Emergency Response Team / Coordination Center (TWCERT/CC), ensuring that information security risks can be identified and addressed at the earliest possible time.
|
Software and Hardware Control |
 |
 |
 |
 |
|
Information Security Incident Reporting Procedure |
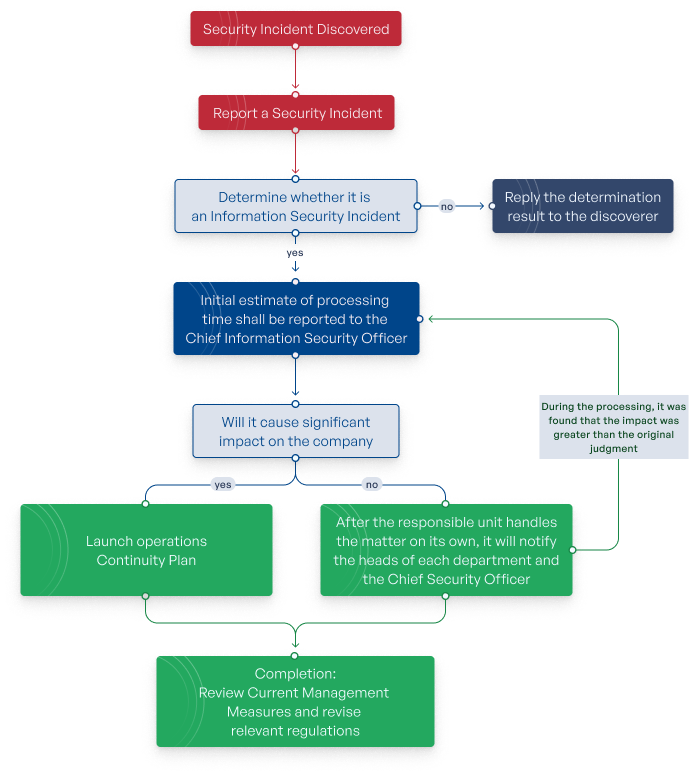
Giant employees are required to promptly report any security incidents to the responsible unit. The unit will assess whether the incident is a security issue and decide whether to report the findings to the discoverer or escalate the matter to the Chief Information Security Officer. Incidents are classified into four levels based on their severity and the impact on the company. Depending on the severity, the "Business Continuity Plan" may be activated, or the incident may be handled through standard procedures. After the incident is resolved, relevant regulations and operational procedures are reviewed to prevent similar incidents from recurring. Regular statistics and analysis of security incidents are conducted to reduce the frequency and impact of future incidents.
 |
External Link Disclaimer
You are about to leave Giant’s website. We have provided this link as a courtesy, but it is no way an endorsement by Giant, and we are responsible for its content. Please understand that when you leave our site, our Privacy Policy is no longer in effect.


